Project Blue Sky
Fortifying Security Enhancing Experience - UX Case Study
Introduction
Sky is an online platform that offers a wide range of services to its users. With the increasing importance of security in today's digital landscape, the decision was made to enhance the platform's security measures by implementing Multi-Factor Authentication (MFA).
This case study will delve into the UX design process undertaken to seamlessly integrate MFA into the platform, ensuring a balance between security and user experience
Objective
The primary goal of this project was to implement MFA while maintaining a user-friendly experience. We aimed to enhance security without causing friction in the user journey, ensuring that users feel confident about the protection of their accounts while still enjoying a smooth and accessible platform.
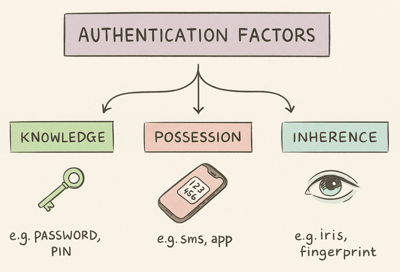
Design Process
In adopting the Double Diamond design process for our MFA Implementation, we navigate through divergent and convergent phases, ensuring a holistic exploration of user needs and security requirements, followed by focused iterations to craft a seamless Multi-Factor Authentication experience tailored to diverse user personas on the Platform.
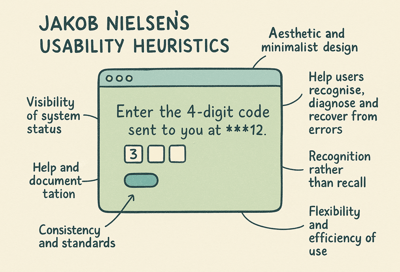
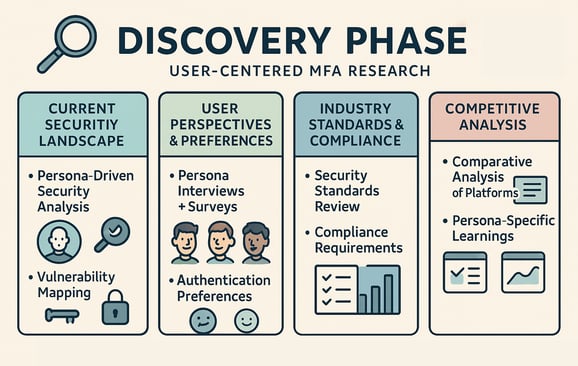
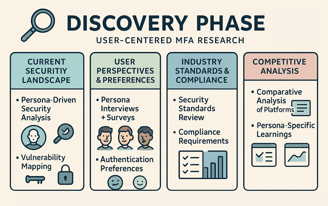
Discovery Phase
Current Security Landscape
Persona-Driven Security Analysis: Analyzed the security landscape through the lens of identified personas.
Vulnerability Mapping: Identified potential vulnerabilities through a persona-centric approach.
User Perspectives and Preferences:
Persona Interviews and Surveys: Conducted interviews and surveys tailored to diverse personas to gauge their attitudes towards security.
Persona-Specific Authentication Preferences: Unearthed insights into individual personas' preferences regarding authentication methods.
Industry Standards and Compliance:
Security Standards Review: Examined current industry security standards with a focus on how they align with each persona's expectations.
Persona-Specific Compliance Requirements: Identified legal and compliance considerations specific to each persona group.
Competitive Analysis:
Persona-Centric Comparative Analysis: Explored how other platforms catered to the security needs of personas similar to the Platform.
Persona-Specific Learnings: Extracted insights from success stories and pitfalls relevant to each persona group.
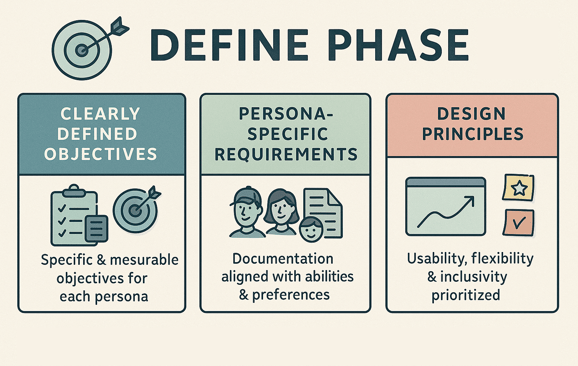
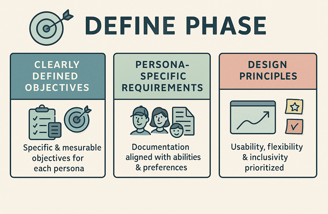
Define Phase
Clearly Defined Persona-Centric Objectives: Specific and measurable security objectives aligned with the unique needs of each persona.
Persona-Specific Requirements Documentation: A detailed documentation of security requirements tailored to the preferences and abilities of each persona.
Adopted Design Principles: Clear design principles that prioritize usability, flexibility, and inclusivity for each persona group.
Ideate Phase
In the Ideate phase, our focus shifts from understanding and defining to crafting actionable solutions for Multi-Factor Authentication (MFA) on the Platform. This stage involves translating the insights gathered during discovery and definition into tangible design elements that seamlessly integrate security measures while prioritizing the diverse needs of identified personas.
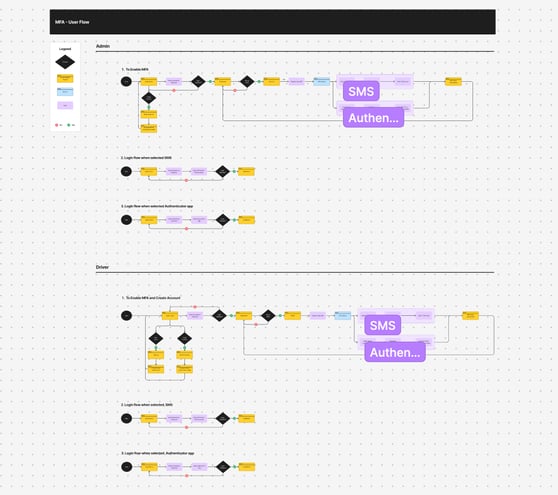
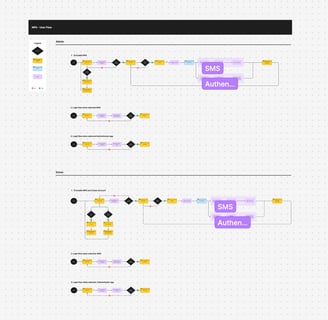
Design
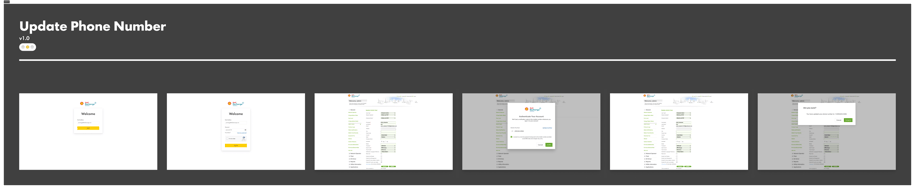
Initially, I sketched a low-fidelity wireframe on paper. After making a few iterations and corrections, I proceeded to design the prototype using Figma for initial testing.


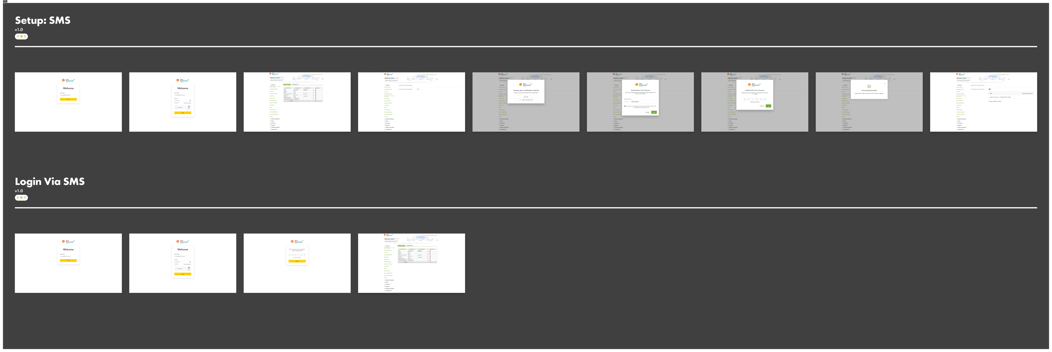
Usability Test
After completing the wireframe, I tested the prototype with six representative users to assess its seamless user experience. The test was conducted via a team call, during which participants were assigned specific tasks, and I observed their navigation through the application.
User initiates the MFA setup process, selecting preferred authentication methods (e.g., SMS, authentication app) as per their preferences.
User assesses the clarity of instructions provided during the MFA setup, noting any confusion or areas that require improvement.
User interacts with visual elements such as icons and buttons, evaluating their intuitiveness and effectiveness in guiding through the MFA process.
User intentionally provides incorrect information during the setup to observe the system's response and assess the effectiveness of error handling.
User explores the option to switch between different authentication methods, testing the flexibility of the system in accommodating user preferences.
Feedback
Offer the ability to update the phone number when displaying it.
Implementation Feedback
The feedback gathered from usability testing was carefully taken into account, leading to the implementation of the following improvements.